A Dive into the WebAuthn API in Joomla 4
Have you noticed there’s a new Web Authentication button on the new Joomla 4 login screens?
It's there because of Joomla’s new WebAuthn API that allows secure logins with a FIDO certified key. So, let's take a dive into passwords, security, and WebAuthn, and find out how to activate it on your user account in Joomla 4.
If you've checked out Joomla 4, then you already know the admin area's had a revamp, which includes the user and administrator login screen. But, have you noticed that it's different depending on whether you're connected to a website that's using https, or http?
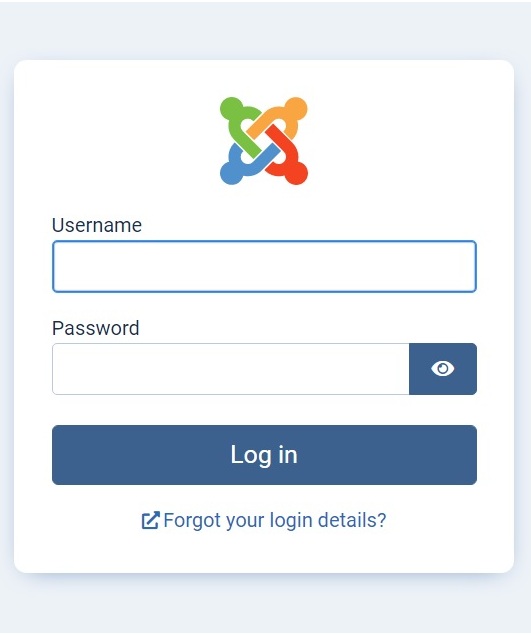
Non secure http login screen
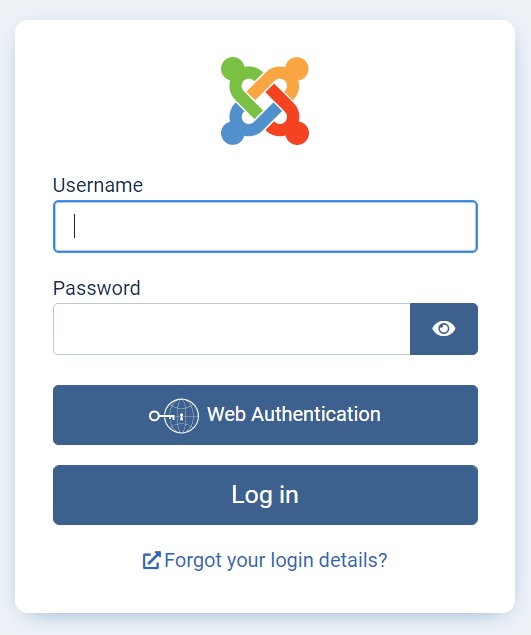
Secure https login screen
If you’re connected securely via https, then Joomla’s new Web Authentication Button becomes visible. This button is part of Joomla’s new WebAuthn feature, which allows you to login securely with a WebAuthn (FIDO2) key, instead of using a password.
Passwords are the bane of everyone’s life.
With technology increasingly becoming intertwined with everyone’s life, your password list is forever growing. If you follow the general password advice of not using a password that’s easy to guess, not writing it down but memorising it, and using a mix of letters, numbers, and special characters, you’ve got a tough job in front of you.
Did you know that:
“123456” is the most-used password in the world!
For a bit of fun, here’s a list from Nordpass of the top ten passwords used worldwide in 2021. The list also shows how long it takes to crack them in a targeted brute force attack, and how frequently they were used, as seen in 2021.
- 123456 - Takes less than one second to crack, used more than 103M times
- 123456789 - Takes less than one second to crack, used more than 46M times
- 12345 - Takes less than one second to crack, used more than 32M times
- qwerty - Takes less than one second to crack, used more than 22M times
- password - Takes less than one second to crack, used more than 20M times
- 12345678 - Takes less than one second to crack, used more than 14M times
- 111111 - Takes less than one second to crack, used more than 13M times
- 123123 - Takes less than one second to crack, used more than 10M times
- 1234567890 - Takes less than one second to crack, used more than 9.6M times
- 1234567 - Takes less than one second to crack, used more than 9.3M times
Are you guilty of using weak passwords? Is yours on this list?
Good password habits are like any good habit. They're easier said than done!
More accounts and more apps create more passwords, which in turn creates more opportunity for theft and data breaches. So, the need for more secure login processes is paramount. Which is something that GoDaddy, T-Mobile and DailyQuiz wished they’d had, as they each suffered from giant data breaches in 2021.
Don’t think it won’t happen to you. You don’t need to run a multinational conglomerate, even your small Mom & Pop website could be attacked and used as a host for spamming and phishing purposes. Don’t let weak passwords make your Joomla website an easy target for hackers.
Of course, easy to remember passwords that are weak by nature, are attractive to use. More secure passwords are the sensible option, but being difficult to remember, we need help.
Over the years, we’ve seen different solutions to this problem, but there are pros and cons for each. Two of the more common solutions to help protect your passwords, and therefore access to your accounts, include password managers and 2 factor authorisation.
Password Managers
There are both free and paid for password managers and they all work similarly.
Password managers need to be installed on your PC, phone or tablet, and are used to store your passwords. Most use 256 bit encryption to do this. You login to the password manager with a ‘Master Password’ and they will remember, or generate secure passwords for all of your online accounts. As well as log you in automatically to those accounts.
However, there are some drawbacks. Most notably: You’re entrusting your data to a third party. If you lose your master password, you lose access to all your accounts. Your master password is not secure from keyloggers and phishing attacks.
Two Factor Authentication (2FA)
Two factor authentication has been around for a while now. In fact, Joomla was the first CMS to implement this way back in November 2013 with the launch of version 3.2.0. It’s a way of adding another layer of security to the login process. So, not only do you need your username and password, but also a one time generated key. The keys are generated by an external service such as Google’s Authenticator and then the key’s sent to your mobile phone. You can then manually input it to the Joomla login screen.
As with using a password manager, there are also some issues regarding security and access to your website administration area. Although fewer than using a password manager. This is because of the key logger / phishing aspects being removed from the equation, as the codes generated for two factor authentication are single use.
Although you do still have to remember the password and keep it secret. However, someone without the ‘extra key’ still can’t access your account, even if they’ve got hold of your password and username.
The main issues with two factor authentication begin with the time needed to login as it increases. There are more opportunities to make mistakes. You may lose access to the authenticator service you’ve chosen to use. Or, you may lose access to the device you use to access that authentication service. Another issue could be the emergency access codes that can be pre-generated, and then printed out for potential future use. An unauthorised person who found them while rummaging around on your desk could use these to access your account.
Now there’s a third:
WebAuthn & FIDO2
We now have a new option to login in Joomla, WebAuthn.
WebAuthn is an emerging web technology that’s been around for a little while, but it’s now gaining traction with more and more websites and applications offering this secure form of logging in.
WebAuthn, or The Web Authentication API, is a project of the World Wide Web Consortium (W3C) and FIDO, which is an international community. Community members comprise of member organisations, full-time staff, and the public who work together to develop web standards. And, some of the world’s biggest players on the internet like Microsoft, Apple, Yubico, and Google are behind it.
The WebAuthn API allows websites to register and authenticate users using public/private key pair cryptography, instead of using a password.
The WebAuthn API makes it easy to take advantage of the strong authenticators now built into devices, like Windows Hello or Apple’s Touch ID.
WebAuthn works by securely storing the private key on the user's device or application, your FIDO2 key in this case. Then a randomly generated public key is stored on the server/website/app. When you login using your FIDO2 WebAuthn key, the server then uses that public key to prove your identity, by matching it to the one stored on your key.

Because the public key stored on the server is useless without the private one, it means that the contents of databases are less attractive targets for hackers. Which is a bonus.
WebAuthn comes in different forms: fingerprint scanners, keys and mobiles are common FIDO devices.
So, let’s take a look at setting up your Joomla 4 user account to work with a WebAuthn FIDO2 certified key.
Logging into Joomla with a FIDO2 WebAuthn Key
The first thing you’ll need to do is to get hold of a FIDO2 certified key. I picked up a basic USB one from Amazon for only £15. It’s made by Thetis, but others are available. Yubico has a bigger range, which also covers different WebAuthn protocols such as FIDO2, U2F, Smart card, OTP, OpenPGP 3. Keys are also available with different connectors; USB-A, USB-C, NFC, and Lightning. So, you’ll have to do your research and choose a solution that suits your own applications.

Fire up your browser and head over to your Joomla login screen. Or, if you have access to the admin area of Joomla, https://your-website.com/administrator (or, if you’re hiding the admin login URL, go there instead)
Login as normal with your username and password. Once logged in, click on the ‘User Menu’ button in the top right corner of your screen. Then, in the drop-down menu, click on ‘Edit Account’.
On the next screen, if you’ve logged in via https, you’ll see a tab labelled ‘WC3 Web Authentication (WebAuthn) Login’. Go ahead and open the tab.
To add your FIDO2 key, click on the ‘Add New Authenticator’ button. A pop-up will then appear, telling you to insert your key and touch it. So, insert your key into a USB/Lightning slot and touch it. Or, as on my Thetis key, press the button. Make sure that you check the instructions that came with your key, as this process could be different, or you may need to register for an account with the key’s manufacturer first. I didn’t have to, but you may need to depending on what type of FIDO2 key you have.
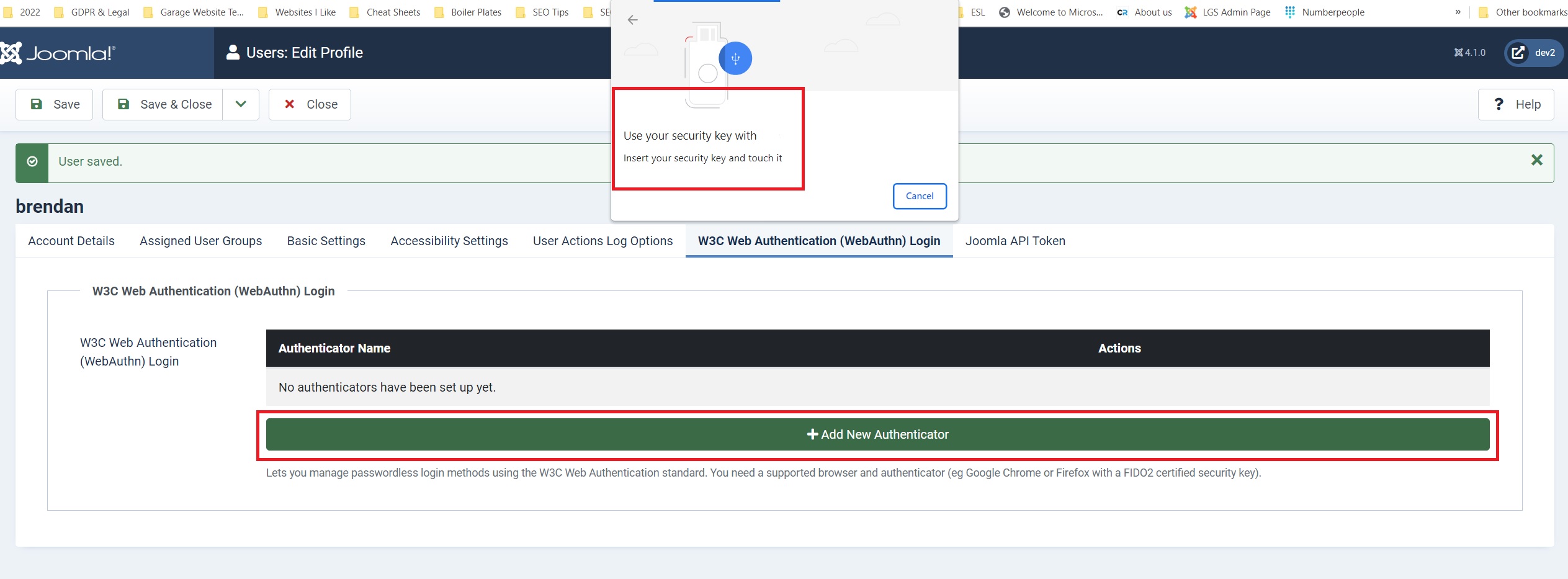
Wait for a few seconds while your key, browser, website, and server sync your cryptographic private/public keys for login. The next screen that appears will inform you it has registered a new key to your account. It’ll have a generic key name associated with it at this stage. So, let’s change it to something more personal.
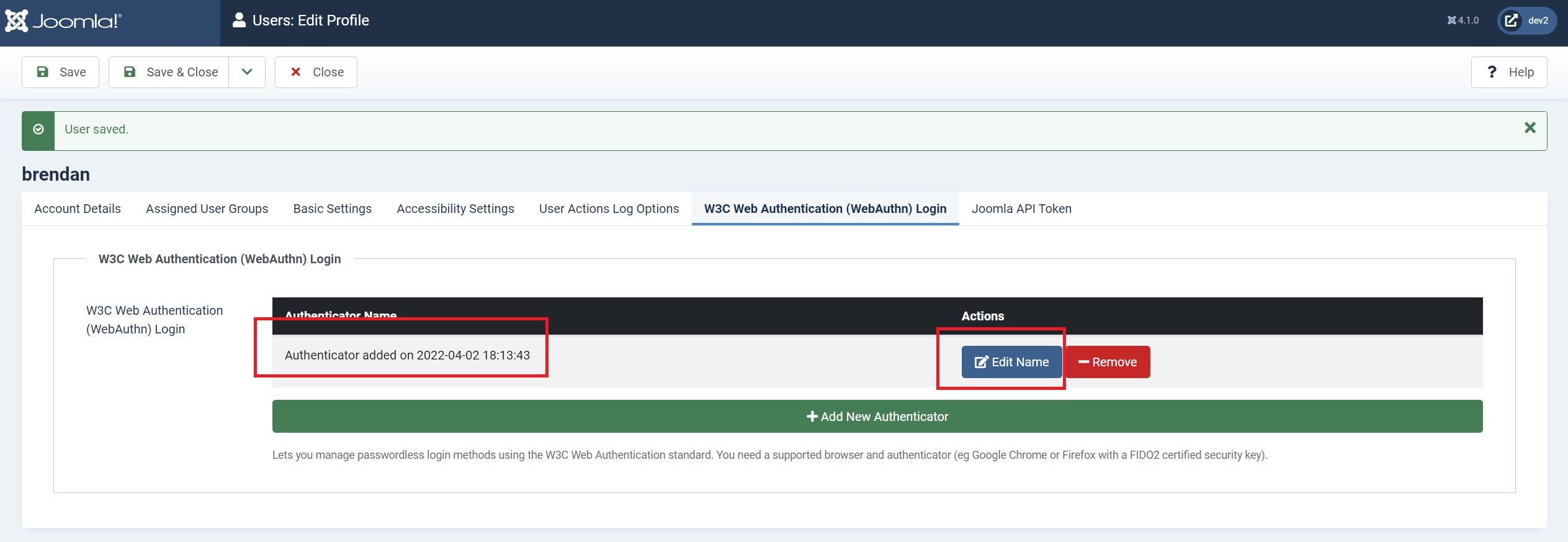
Click the blue ‘Edit Name’ button and enter a new key name in the field, then save it.
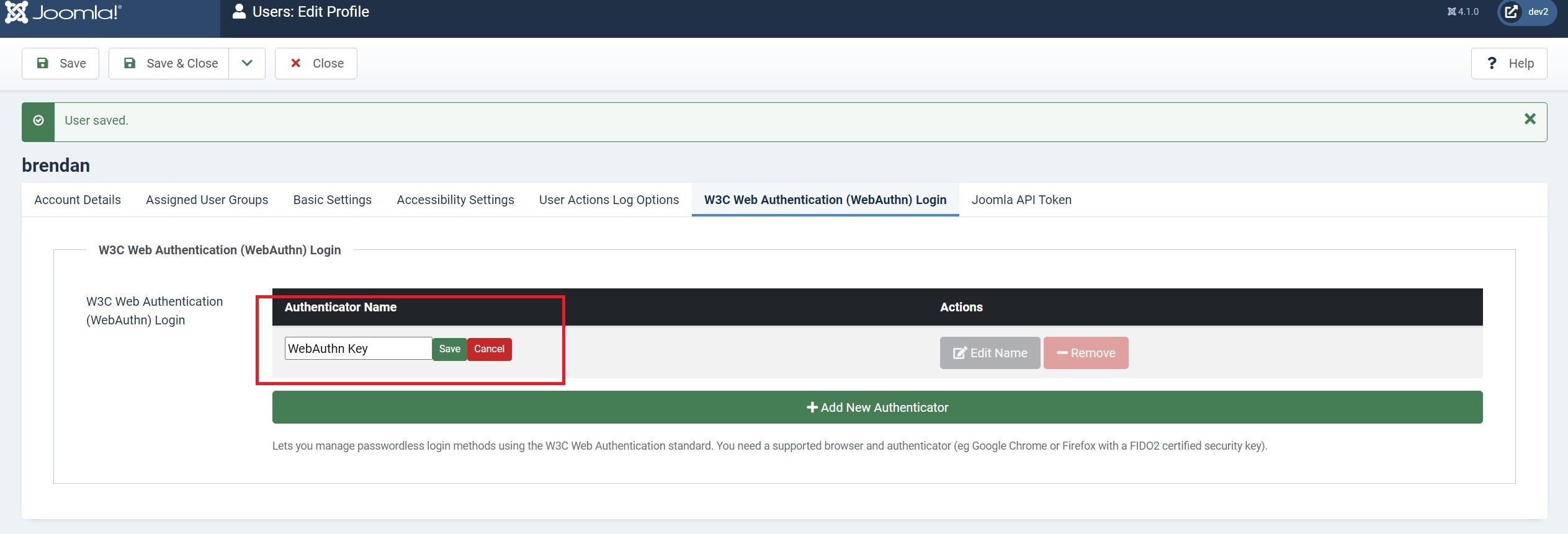
And that’s it. You’ve now set up your user account to work with your new key. Now’s the time to test it out, so log out completely, return to the login page, insert your key into a USB/Lightning port, enter your username and click the ‘Web Authentication’ button.
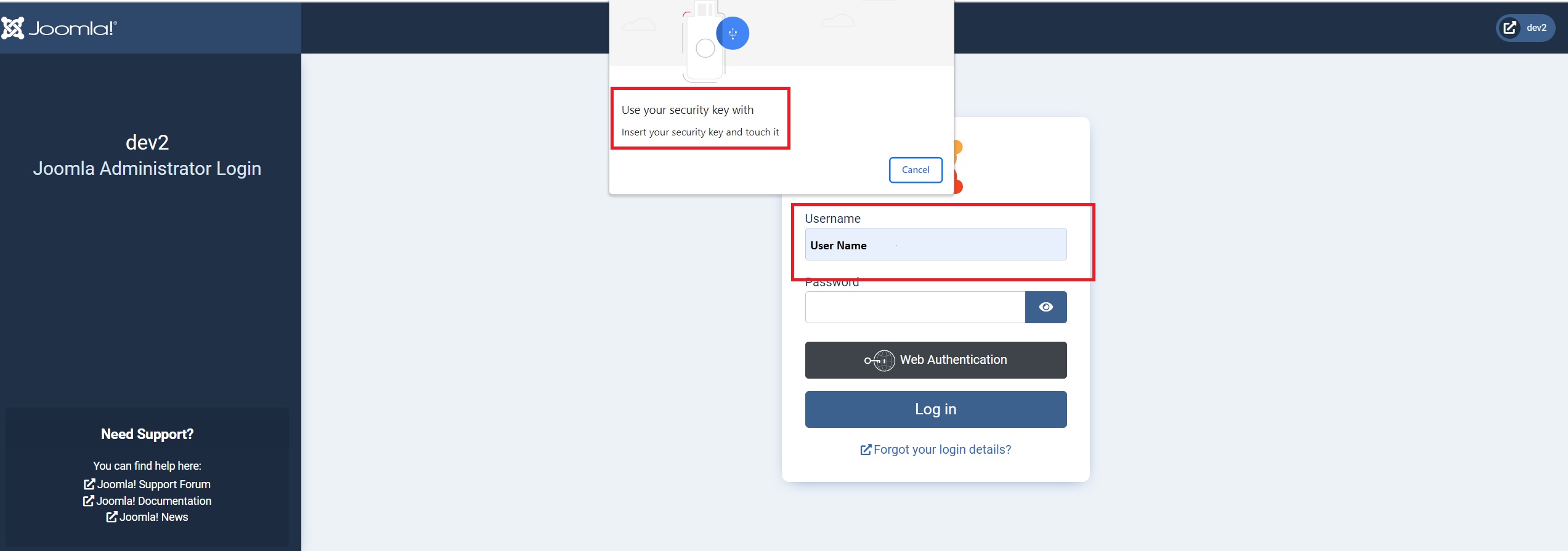
If everything’s gone well, you are now logged into your user account in Joomla.
Some Questions & Advice
If you’ve read this far, and you’re anything like us, you’ve probably now got some questions about using this new API in Joomla 4. Although WebAuthn and FIDO2 keys are secure, no system is perfect. There will always be situations and exceptions to the rules. The following are questions I have had while researching this article about Joomla’s new WebAuthn Login API. Some there are answers to, others I’m still wondering about!
Can an admin remove my key from my account?
No, Joomla’s administrators cannot add or remove authenticators on behalf of users. Users must login, and set up their own devices.
Do you need to register your key with the key manufacturer?
My Thetis key did not require me to register my key with them prior to its use, but other keys may have different processes.
Is my private key secure?
Yes, the key pair is generated on the FIDO2 device, which is typically a USB security key. The private key is securely bound to the device.
Will my password still work?
Yes, and this is one aspect that I think needs further thought from Joomla to fully take advantage of the security advantages of using a FIDO2 WebAuthn Key.
While still having a password linked to your user account could be handy if you lose access to your key, it still represents an opportunity for hackers to access your account. Although if you stop using a password while logging in, keyloggers and spoof phishing websites won’t be able to steal your login data. But brute force attacks could still work.
The work around for this, at the moment at least, is to create a new strong password after you’ve added your key to Joomla. A password that’s almost impossible to break, and impossible to remember. So write it down, don’t copy/paste it (key loggers can’t read your handwritten notes. Did you know that even Microsoft has a built in key logger in Windows 10 & 11?). Nicholas, from Akeeba, suggests that it would be a good idea to use a 128 character password to make it almost impossible for a brute force attack to access your account successfully.
If you are the super-user for your Joomla website, it might make sense to upgrade the standard password requirements for users to something more secure, as standard. Increase the required password length from 12 characters to at least 20, and include numbers, special characters, and capitals. You can find these in Users > Options > Password Options.
What happens if I lose my key?
You won’t be able to use it to log in securely to your Joomla user account. You’ll have to use the new, long, secure password you created after you registered your FIDO key to your Joomla account. If this happens, don’t forget to create a new super strong password to replace the one you've just used, and write it down just like last time.
A lost WebAuthn FIDO2 key does not pose a security risk. The keys are designed to be anonymous to public online services, and no information about your identity or accounts is stored on the key itself.
What happens if my key gets wet?
This could be a serious consideration if you keep your key in a pocket, that could get wet. Or, you drop it in a puddle! I can’t find any information about my Thetis key, but Yubico keys state they are rated IP68, which means they resist dust and are good for an hour submerged in 1.5 metres of water.
Can I login to multiple websites with one key?
Yes, but the amount will vary from manufacturer to manufacturer. It depends on the amount of memory used in your key.
Should I use a more secure username?
Yes. It's always good advice to make it more difficult for the unscrupulous to access your account. john2!4*6smith instead of johnsmith is much better. If you use a strong username, it will make it more difficult for someone else who may have access to your key to use it maliciously.
Should I have a backup key?
It’s not a bad idea. Although the keys have no batteries or moving parts and could be IP68 rated, and crush resistant, they could still stop working, get lost, or become damaged.
Can I have 2 keys on one Joomla user account?
Yes, you can register multiple keys to your Joomla user account. So, having a backup makes sense.
Can my key be cloned or copied?
FIDO2 keys are secure, therefore by design can’t be copied. If they can’t be copied, it stands to reason that cloning won’t be a problem either.
Once logged in, do I need to leave my FIDO2 key in the USB/Lightning port?
No, once you’re logged in, there’s no need to leave your key inserted in the USB/Lightning port.
Can I use my FIDO2 key on Linux?
Yes, and no. Some newer versions of Linux have built-in support for security keys out of the box. Many older versions do not, and you will have to make a minor system configuration change to get your key working. Google is your friend here!
Which browsers support my FIDO key?
Things are improving rapidly. When the original Joomla documents were written for this feature, support was a little sketchy.
But now, as of March 2022, desktop browser support is a lot better with all the key players on board. Although mobile browsers are still trailing behind, except for Firefox.
| Browser | OS | Supported |
|---|---|---|
| Edge | Windows | FIDO2 |
| Chrome | (Windows / Mac / Linux) | FIDO2 & U2F |
| Firefox | (Windows / Mac / Linux) | FIDO2 & U2F |
| Opera | (Windows / Mac / Linux) | FIDO2 & U2F |
| Safari | MacOS | FIDO2 & U2F |
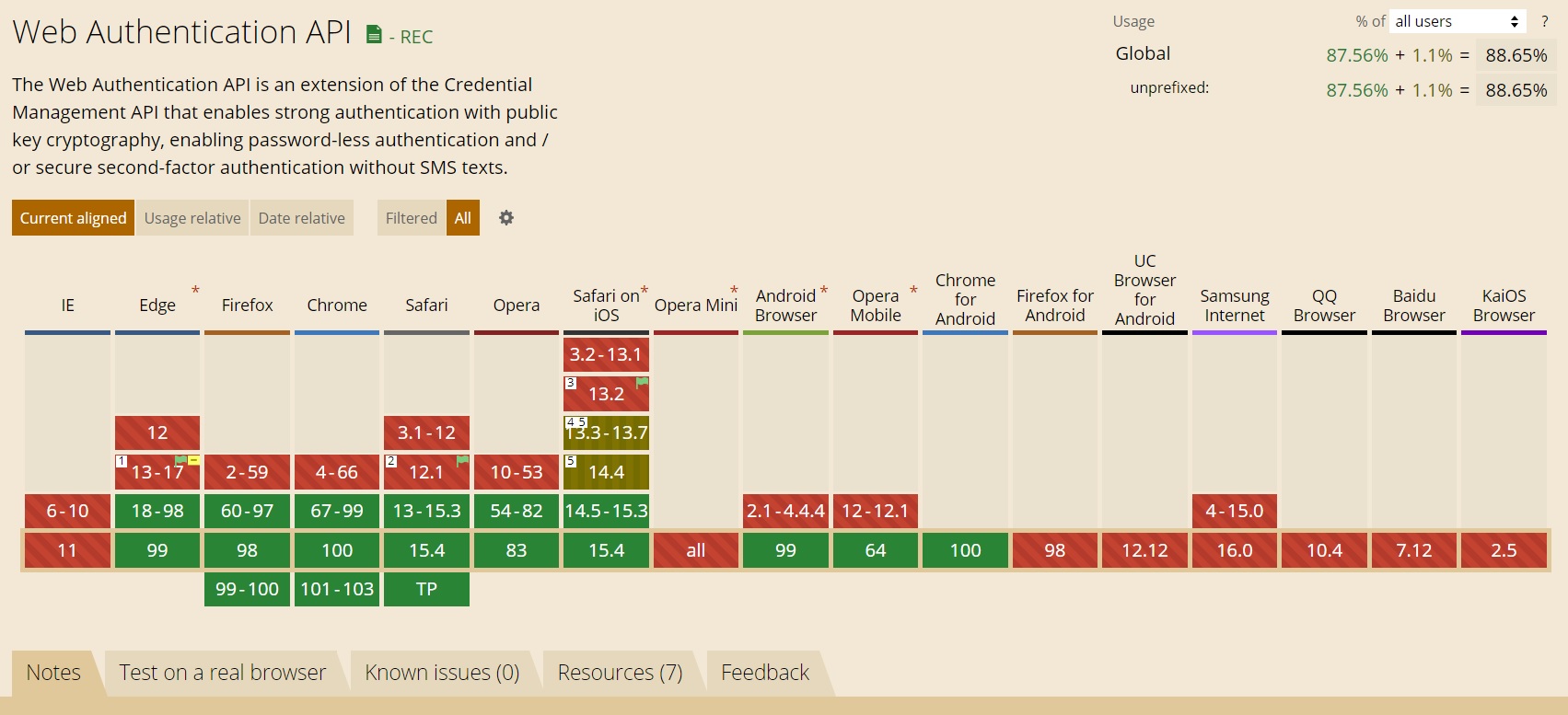
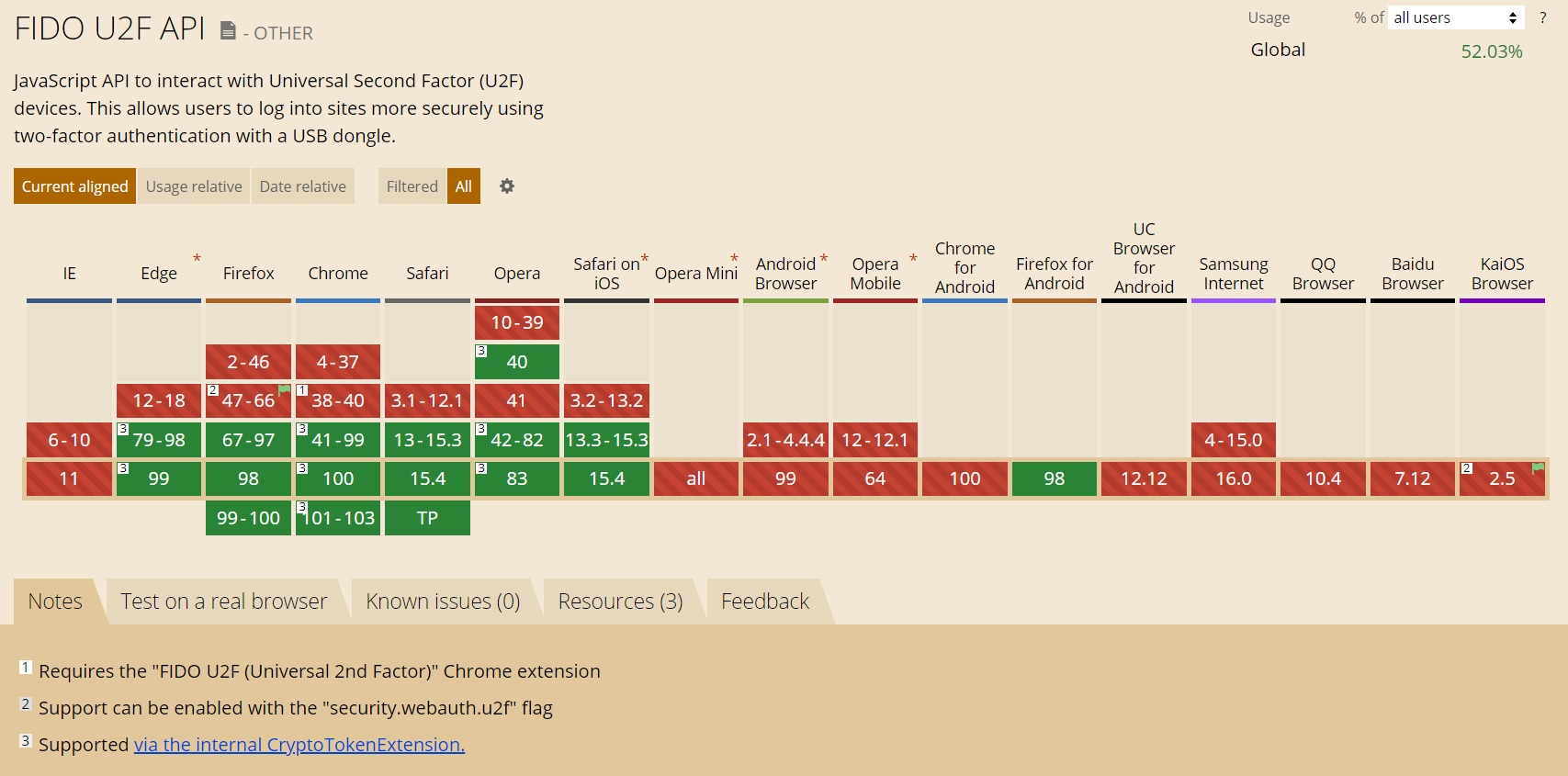
Here are the usage stats form caniuse.com for both WebAuthn and Fido.
WebAuthn
https://caniuse.com/?search=webauthn
FIDO
https://caniuse.com/?search=fido
What about GDPR?
As FIDO keys only store cryptographically paired private/public keys, and no other information, they do not share any personally identifiable information with any FIDO services or computers they are registered with. Therefore, they are GDPR compliant.
Apart from logging into my Joomla account, what else can I use my WebAuthn FIDO2 key for?
There are literally thousands of websites that use this type of secure login system. Joomla being the best, of course. Here’s a few from Yubico’s list of websites and apps that support the WebAuthn FIDO2 protocols.
Cloud single sign-on
Secure instant login to millions of sites and applications.
Password Managers
Protect and manage your passwords across the internet.
Shield personal, sensitive data in your inbox.
Social Media
Protect your reputation by securing your social profiles.
Gaming
Keep your hard-earned gear and reputation in the right hands.
Developer tools
Safeguard your code and intellectual property from hackers.
Cloud Storage
Confidentially store pictures and other sensitive files online.
Crypto Currency
The safest way to store your crypto currency on an exchange.
Computer access
Prevent unauthorised access to your offline computer.
You can even use your WebAuthn FIDO2 key to access your Tesla Account!
Conclusion
As with any emerging or developing technology, there’s a lot of conflicting advice out there on Google. Much of it’s now old, out of date, and insignificant. If you’re looking to login to your websites and apps securely, take the time to find the most recent information, at least as far as compatibility goes.
I think that any advance in technology that helps to keep your online activities safe and secure is a bonus. Especially when we are so useless at protecting ourselves with strong passwords. It reminds me of the look on my clients’ faces when I hand over the login info to their new websites. It’s that point when they realise they can’t use ‘fred123’ as a password!
Personally, I always use strong, very forgettable passwords, but I’m sure I’m in the minority. So, this new feature that allows secure login to your Joomla Account is great. Anything that removes phishing, key logging, and reduces brute force attacks from the equation is cool by me. Just don’t lose your key!
From a developer’s point of view, it would also be a good idea to include a couple of FIDO2 keys already registered to the Joomla website when you hand it over to your client. If you did that, there wouldn’t even be a need to hand over a password. Although they could still generate one themselves via the lost password function of Joomla if they needed one for some reason.
Now that the WebAuthn API is included in the core functions of Joomla, I’ll certainly be using it as an option to login to all of my Joomla 4 websites, as well as my clients’ websites. There’ll be no more hunting for the latest version of a long since forgotten password on one of several hard drives.
Lastly, a big thank you to Nicholas from Akeeba for his insight and information regarding this new Joomla feature.
Icons for Webauthn diagram from www.flaticon.com
German translation of this article: https://www.jug-zueri.ch/artikel/eintauchen-in-die-webauthn-api-von-joomla-4
Some articles published on the Joomla Community Magazine represent the personal opinion or experience of the Author on the specific topic and might not be aligned to the official position of the Joomla Project
By accepting you will be accessing a service provided by a third-party external to https://magazine.joomla.org/
 Community Magazine
Community Magazine 
Comments 1
This in a excellent article, I do have however a few minor points to make as the developer who contributed this code to Joomla
You don't necessarily need a FIDO2 key. FIDO keys (a.k.a. security keys or U2F keys) are still supported. FIDO2 keys are better as they support more secure algorithms. If you have an old FIDO capable hardware authenticator it will still work with WebAuthn.
The username is not an authentication factor, it must always be considered public information. That's why logging with a username and a password is called single factor authentication: the only authenticating factor is the password. Treating the username as a secret is a remnant of the days of yore, before Two Factor Authentication and before WebAuthn.
You said that Linux may not have good support. While that was true ten years ago when FIDO was in its infancy, this is no longer true. If you are using any supported Linux distribution (i.e. a Linux distribution published the last 5 to 8 years) FIDO / FIDO2 keys are fully supported without having to mess with your udev rules. Since most people will be using an Ubuntu or RedHat derivative: rest assured that anything published from 2016 onwards supports FIDO and FIDO2 keys just fine.
Finally, and most importantly, WebAuthn does not require you to have a separate hardware authenticator. It can work with any FIDO2 authenticator, including the built-in authenticators in your device! The code we've shipped with Joomla works with TouchID and FaceID on Macs, iPhones and iPads. It also works with Android fingerprint authentication on Google Chrome on modern Android versions (Android 9 and later, if I recall correctly). It does not work just yet with Windows Hello, I need to contribute a small change in the code to do that.