Passwordless authentication for secure, fast and easy logins in Joomla! 4
Joomla! 4 introduces a plethora of new and exciting features. While most of them are very visible, giving you new ways to build and use your sites more easily, there's an abundance of features designed to enhance the security of your site. Today we'll be talking about WebAuthn, a feature that has the unique distinction of belonging in both categories: it makes your site login more secure and easier at the same time.
Passwords get sites hacked
There's a widespread myth that only high value sites are at risk of being hacked. While it's true that high value sites are more likely to be subjected to targeted attack campaigns, it doesn't means that smaller sites won't be attacked. Cybercriminals relish at opportunistic attacks against undefended sites which can be used to send spam or phishing emails, host malware or become unwitting accomplices to their crimes as part of a botnet.
The most common avenue for compromising a site is embarrassingly simple: an insecure or reused password, discovered by an automated attack tool. There are plenty of lists out there with known, real world passwords discovered from past leaks of major sites. These opportunistic attacks hinge on the human propensity of using easy to remember passwords and reusing them across different sites and services. While vulnerabilities in outdated software may make discovering such passwords easier or provide other ways of obtaining illicit access to the site, they are neither common nor necessary to compromise a site.
Beyond that, should an attacker obtain a copy of your site's database – exploiting a vulnerability in Joomla or a third party extension – they have a copy of all usernames, email addresses and passwords known to Joomla. Joomla has been upgrading the way it stores passwords in its database, using stronger hashing algorithms which are harder to crack. Despite that, the advent of cloud computing providers and the relatively cheap price they offer for GPU computing, the ideal type of computing power for cracking passwords undermines these efforts – at least to a certain extent.
Joomla has offered Two Factor Authentication (2FA) since version 3.2 as a practical means to reduce the impact of bad passwords. However, 2FA is cumbersome as it requires entering yet another piece of information via another device or application. Furthermore, the way the most popular 2FA software (Google Authenticator) is implemented has caught many a user by surprise: if you reset or change your phone you lose access to all your stored 2FA, locking you out of your sites and necessitating some “database surgery” to regain access. On top of that, it doesn't fully solve the problem that just like a password it can, too, be unwittingly divulged to an attacker or stolen by malware.
None of these challenges are unique to Joomla. They are inherent weaknesses in using passwords as a means for authentication (logging in). While using a password manager to generate and store a different, randomly generated, long and complex password for every site and using Two Factor Authentication help mitigate the risks of using passwords for authentication, this solution is complicated and will put off the users who need it most.
Enter public key cryptography
Introduced in the 1970s, public key cryptography has solved the problem of exchanging information securely. It's based on two very long numbers which are mathematically entwined. They are called the Public Key and the Private Key. A Public Key and its entwined Private Key are called a Key Pair. What you encrypt with one key can only be decrypted with the other. Having one of the keys does not compromise the security of the encryption. In fact, you are supposed to share the Public Key with everyone, be it friend or foe. The mathematics behind Public Key Cryptography dictate that having one key does not let you find out the other in any practical way, even with today's abundance of computing power.
Public Key Cryptography underpins the web as we know it. It is what is used in HTTPS, making secure information exchange – like entering your credit card online – possible and practical.
It turns out that you can use the same technology to replace passwords. In a nutshell, the browser needs to generate a Key Pair and give the Public Key to the server. When it's time to log in, the server sends a chunk of randomly generated data to the browser and remembers it. The browser encrypts it with the Private Key it has kept to itself and sends the encrypted data back to the server. The server decrypts the data with the public key that corresponds to the private key the server claims to have used. It then checks that the decrypted data matches the data it remembered it had sent to the browser. If that's the case, the user is logged in. This process, along with all the necessary controls required for the browser and server to establish mutual trust, is a W3C standard called Web Authentication, or WebAuthn for short.
WebAuthn is secure
Having the browser handle generating a key pair and storing the secret key on the user's device without any further protection would be a fool's errand. Browsers are very complex. Their complexity is a constant and understandable source of bugs, some of which having security implications which could force a browser to divulge its Secret Keys. Beyond that, malware on the user's device could steal the Secret Key from the device's storage or the browser's memory. So while WebAuthn allows the browser to handle all that by itself, in what it calls a software authenticator, it discourages it and instead insists on using secure hardware instead. In fact, most modern browsers either do not implement software authenticators at all or have them disabled by default.
Most modern devices have secure cryptographic hardware built into them. This is usually called a TPM or Secure Enclave. These chips are black boxes even to the device's processor (CPU), the chip that run the Operating System, your browser and everything else. That is to say, all the device can do is send data to the secure hardware and get an encrypted or decrypted message in return. Further to that, secure hardware is unlocked using biometrics such as Windows Hello on Windows 10 (using a fingerprint, face scan or other biometrics), TouchID / FaceID on Apple devices or a fingerprint scan on Android devices. In short, it's not enough to be in possession of a device; you need to use biometrics to prove that you are who you say you are.
Additionally, it's possible to use secure hardware dongles which implement the FIDO2 or FIDO protocols for authentication. These are similar to a TPM or Secure Enclave but instead of being built into the device, they connect to it using USB, NFC or Bluetooth Low Energy (BLE). They are unlocked by pressing / touching a button on them, scanning a fingerprint, entering a PIN on a dongle on the device, providing a PIN on your computer, or a combination thereof. That is to say, having the dongle attached to the device isn't enough. It requires positive interaction with the user, therefore eliminating silent, remote exploitation in case there's a browser bug or your device is compromised (e.g. due to malware). Obviously, if the only protection is pressing a button these devices are like your house keys: if you misplace them they can be used to unlock everything. That's why Windows 10 requires them to be protected with a PIN to even offer you the possibility to use them. Even if they are misplaced or stolen, they will be useless without the PIN that only you know.
The secure hardware used to generate the key pair, be it embedded in the device or an external dongle, is called an “authenticator” in WebAuthn parlance. Your login is, in fact, linked to the authenticator and not directly to the browser you are using. To wit, if you are using a secure hardware dongle such as a Yubico Security Key NFC you can use it across browsers and devices such as your laptop, your phone and your tablet without having to reconfigure each and every browser on each and every device.
The other reason WebAuthn is secure is the fact that the server, in this case your Joomla site, only knows of the Public Key linked to each browser or device used to login to the site. The Public Key is designed to not be secret. You can give it to anyone and everyone without adversely affecting the security of your login! If someone compromises your site they will get the stored WebAuthn public keys which are completely useless on their own right. Unlike password hashes, they cannot be cracked or used in any way to spoof a login.
WebAuthn also links the key pair to the exact domain and subdomain of the site it is generated for. This means that a key pair generated for example.com will not be valid for www.example.com, foobar.example.com or example.net. Likewise, a key pair generated for www.example.com will not be valid for example.com or even foobar.www.example.com. This may sound like a trivial detail, but it protects you from an attacker installing a malicious site on a subdomain of a trusted site to intercept the login.
Finally, WebAuthn hinges on encrypted information exchange. There is nothing to type. The information exchanged is encrypted in its own right, it's transferred further encrypted over HTTPS and it contains controls which let both the browser and server verify that it has not been tampered with. This makes WebAuthn unphishable (you can't be tricked into divulging it to an attacker) and very resilient to network attacks.
In short, WebAuthn is the closest thing to “unhackable” we can possibly get to with current technology. It's not just a replacement for passwords, it's designed to fix everything that is wrong with passwords and then some.
What you need for WebAuthn
I'm very happy to have contributed code to support WebAuthn, which is included in Joomla 4. In order to use WebAuthn on your sites you need to meet the following requirements:
Enable the “System - WebAuthn Passwordless Login” plugin. This plugin is enabled by default and is what implements WebAuthn in Joomla, including authenticator management and login.
HTTPS with a valid certificate. Your site must always and only be accessible through HTTPS. You can do that by setting Force HTTPS to Entire Site in your Global Configuration. Make sure you have a valid SSL certificate. Most hosts allow you to get one free of charge using the Let's Encrypt service. The caveat here is that WebAuthn will NOT work if you are developing locally or on a temporary URL. That is to say, WebAuthn is something you should only enable on your live site.
A browser that supports WebAuthn. All up-to-date versions of Google Chrome, Safari, Mozilla Firefox, Microsoft Edge, Opera, Brave and others support WebAuthn. I strongly recommend using Google Chrome, Safari, Mozilla Firefox, Microsoft Edge on your desktop, Safari on Apple devices and Google Chrome on Android for best support of embedded authenticators.
An authenticator. There are two kinds of authenticators you should be using:
- Embedded authenticators. If you have a device running Windows 10 version 1903 or later, Android Pie or later, macOS Big Sur or later, or iOS/iPadOS 14 or later and it has biometric authentication (fingerprint, face scanning with an infrared camera, TouchID or FaceID) you can use your device itself as a WebAuthn authenticator. These devices have a secure cryptography chip, TPM or Secure Enclave, and the necessary support in the Operating System to use it with WebAuthn.
- Secure hardware dongles. This is the best solution for older or cheaper devices and devices running Linux and other Operating Systems. You can use any hardware dongle that supports FIDO or FIDO2, the latter being more secure. You can find them on local and online retailers. They typically cost between 10 and 30 Euros.
There are pros and cons to each type of authenticator. An embedded authenticator has no additional cost as it's embedded in your device. Using biometrics is very easy and intuitive, reducing the time to log in. However, should you reinstall your Operating System, reset your device or switch to a different device you will lose access to the secret keys. Of course this also means that if your device is lost or stolen a remote wipe will kill the secret keys as well. Finally, you need to set up WebAuthn for every browser and every device you use – even if it's the same browser across multiple devices or different browsers on the same device.
A secure hardware dongle, on the other hand, is something you can share among all your browsers and devices. You only need to set it up once. Not all devices support the same connectors, though. Your computer may have a USB-A connector, your phone a Lightning connector and your tablet a USB-C connector. There are port conversion dongles and authenticators which support different connections but this adds complexity and cost. Moreover, hardware dongles require interacting physically with them to approve the authentication. This may be cumbersome, depending on your work area layout. If you lose your dongle it can be used to login as you on all sites that support it, unless you have protected it with a PIN. Then again, if you are protecting it with a PIN you need to enter it every time you login which becomes as burdensome as typing a password.
My recommendation on authenticators is to use the embedded authenticator whenever possible. Windows 10, Android and iOS/iPadOS make this dead simple, using the same fingerprint sensor or IR depth camera to scan your face that you use to log in. MacOS relies on the Touch ID sensor, which may be annoying if you're using your MacBook Pro in clamshell (closed lid) mode. However, as of macOS Big Sur, you don't even need to have your MacBook's lid open as long as you have an Apple Watch and configured it to unlock your computer. Logging into a site requires a simple double click on the Apple Watch's side button. That said, I still recommend using a cheap secure hardware dongle protected with a PIN as a backup. Keep it somewhere safe. If all your devices are reset / lost / stolen, you will at least have one viable way to log into your sites without resorting to using a password.
Finally, a caveat. WebAuthn key pairs are tied to the exact domain name of your site as I explained before. This means that www.example.com (with the www in front) and example.com (without the www in front) are considered to be different sites as far as WebAuthn is concerned. I recommend setting up a redirection from the non-www to the www domain name – or vice versa, depending on your preference. Otherwise you will wonder why WebAuthn doesn't work because you will never think to look at the domain name. Trust me, I've done that mistake, repeatedly.
WebAuthn in practice
There are two parts to using WebAuthn: registering an authenticator and using an authenticator.
The first part is how you tell your site which devices or secure hardware dongles to trust for logging you into the site. You only need to do that once for every new site and authenticator.
The latter part is what you will be doing day to day: using your authenticator to log in without using a password.
Registering a WebAuthn authenticator
After logging into your site, go to your Joomla user profile and edit it. In the public frontend there's usually a profile link in the login module. In the administrator backend of the site you need to click the User Menu icon at the top right corner of your site's backend and click on Edit Account. In both cases you will see a section or tab called “W3C Web Authentication (WebAuthn) Login”.
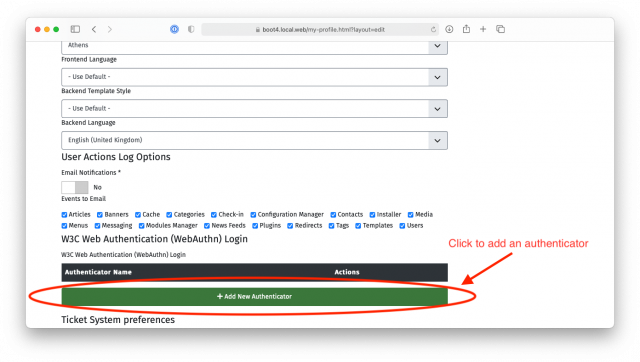
Click the “Add New Authenticator” button. Your browser will ask you to interact with your authenticator. Mobile devices will further ask you if you want to use the integrated fingerprint / TouchID / FaceID or a security key. The former is the embedded authenticator in your device. The latter is for when you want to use a secure hardware dongle. Select whichever option makes sense for you and follow the instructions on screen to activate the authenticator.
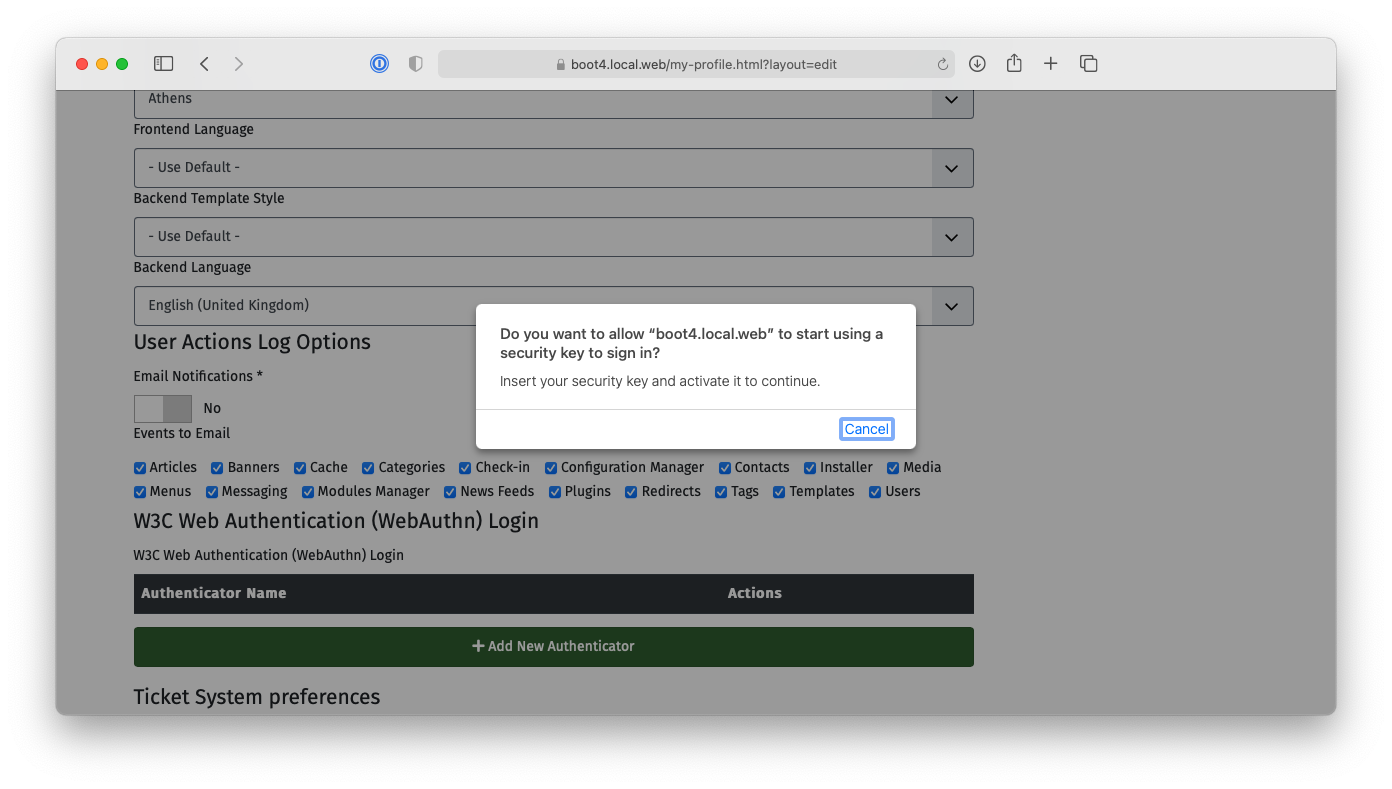
You will now see that a new authenticator was added with a name similar to “Authenticator added on 2020-11-25 10:26:02”. Click the “Edit Name” button to rename it to something more descriptive if you want and click on the “Save” button.
That was it! From now on you can use this authenticator to log in.
Logging in with a WebAuthn authenticator
Frontend login modules compatible with Joomla 4 and the backend login page display a “Web Authentication” button. First enter your username (but not your password!), then click on the “Web Authentication” button.
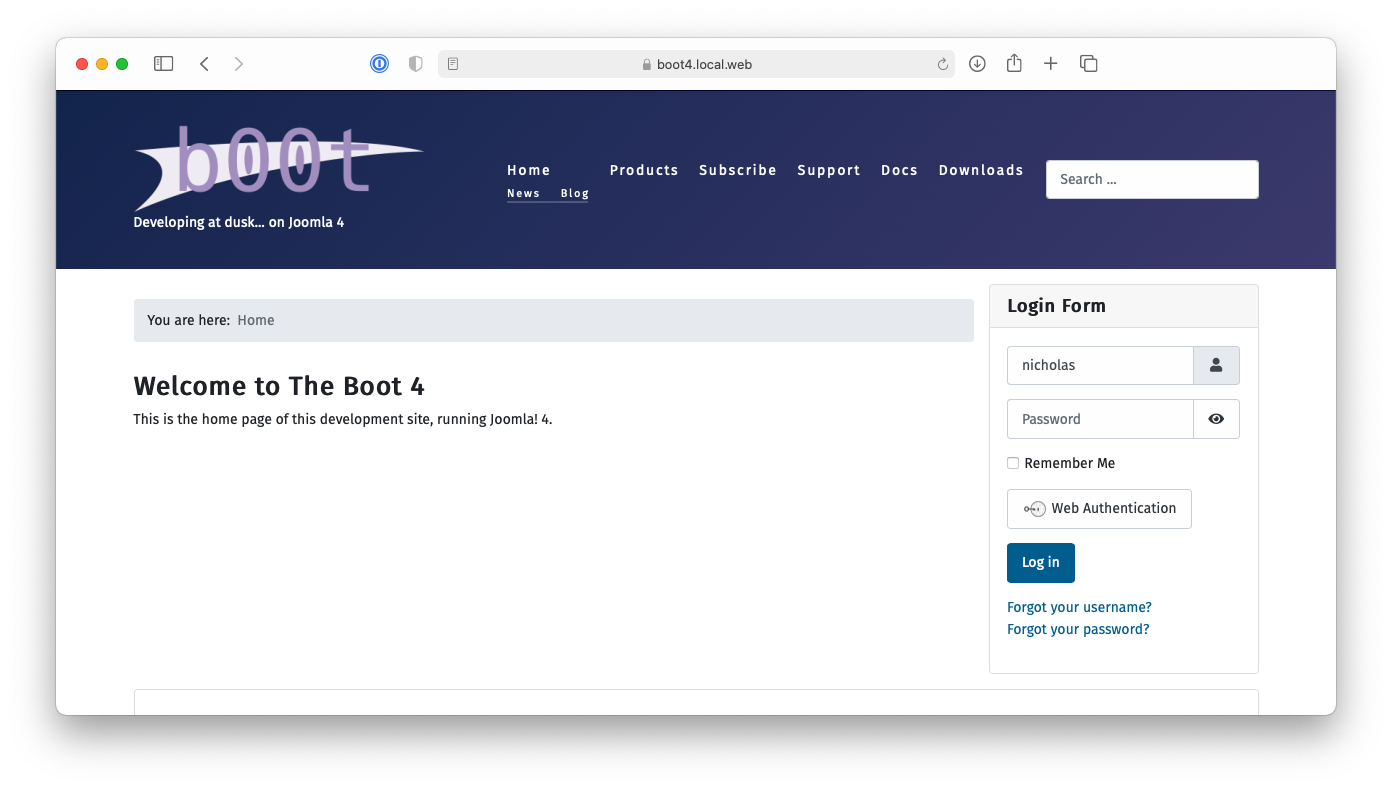
Your browser will ask you to select and activate your authenticator.
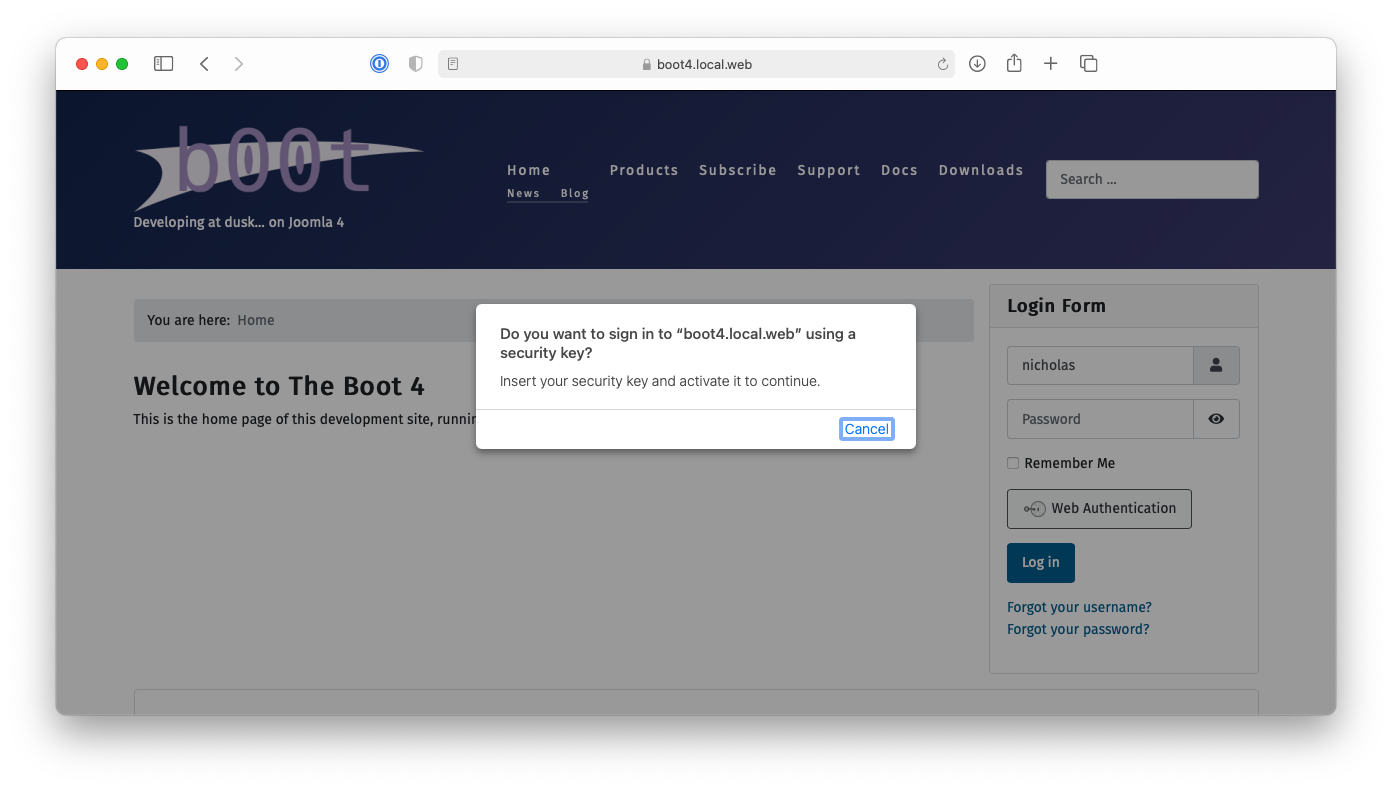
Do that and... you're logged into your site. Like magic!
Do note that at this point in time it's still necessary to type in your username. There is a way to avoid that but we chose to not implement that for a few reasons:
- Only some authenticators (those implementing the newer FIDO2 protocol) support that. This would have limited WebAuthn to the more expensive hardware dongles and devices with built-in secure hardware.
- Most external hardware dongles only support storing usernames for a limited number of sites, typically between 10 and 20. This would limit the number of sites you can use your hardware dongle with.
- Further to the above, there is currently no interface in browsers to manage stored usernames in secure hardware dongles. This would make your rather expensive, secure hardware dongle useless after linking it to a very limited amount of sites.
These limitations are largely teething problems. WebAuthn only became a web standard in March 2019. It is still a very new technology. These limitations are already been worked on the browser and devices side and I expect that they will be overcome by mid-2022. So there's a very good possibility that we can have logins without entering a username. I have already written code to do that, but I cannot contribute it to Joomla until browsers solve these problems.
Obtaining authenticators
If you do not have a device with a built-in authenticator, you will need an external secure hardware dongle. They come in different price ranges and capabilities. You can search in Amazon or your favorite local marketplace for “FIDO2 Security Key”.
I am using either my devices' built-in authenticator or a Security Key NFC by Yubico. The latter isn't exactly cheap but it's the one device of many I tested that gave me the least amount of problems across a number of PCs, Apple devices and Android devices. If you are worried about costs in your organisation, you can order a few keys from different manufacturers and run tests with the devices, Operating Systems and browsers your users are likely to be using so you can find the cheapest option that works for you.
WebAuthn and sharing login information
The one things you cannot do with WebAuthn is share login information, e.g. give someone access temporary access to your site to do troubleshooting. You would have to ship them a physical security key which is slow and impractical.
If you are worried about secure access to your site by third party developers and consultants you should follow a two step process. Ask them to create an account on your site first, asking them to enable WebAuthn on it. When they are done you can change their account's user groups to give them the level access they need to work on your site, e.g. assign them to the Administrator or Super Users group.
Further steps to securing your login
At this point in time Joomla cannot do away with passwords completely. The current architecture dictates that password authentication is always enabled, even when WebAuthn is for an account. This can be addressed with a plugin, one that I might write in the future. But as things stand right now, even when you use WebAuthn in your user account you still need a password for your user account which will allow full access without requiring going through WebAuthn. I recommend using a password manager – even the one included in your browser – to set up a really long, random password for your user account. Use something at least 32, ideally 64, characters long. You will not be using it to login to your site except as a last resort. Keeping it extremely long makes it impractical to guess or even crack in the unlikely event that an attacker gets hold of your database contents.
Further to that, use more than one WebAuthn authenticator. Ideally, one should be a cheap hardware token protected with a PIN. Store it somewhere safe. Don't carry it with you. This would be your backup should all your devices be reset and you no longer have access to the password manager where your long, secure password is stored. This is very unlikely but it can happen. For example, if all your devices are made by Apple and your primary browser where the password is stored is Safari then all your authenticators and password are linked to your iCloud account. If you get locked out of that account, by mistake or malice, you would lose access to your site. Having a backup authenticator is far less stressful than trying to regain access to your sites by making changes to their database contents directly.
Remember that a chain is as strong as its weakest link. Don't let an insecure password, lost access to your devices or a misplaced hardware token be your undoing.
Good security is what you don't need to think about.
In closing, let's reflect on why WebAuthn is a positive step forward for the web and Joomla in particular.
I am a sucker for car analogies. I like to say that WebAuthn is the computer equivalent of a seatbelt. After you use it for a couple of times it becomes a second nature. You hardly need to think about it. It works the same everywhere.
Compare that with the veritable security circus act of using passwords. Every time you login to a site it sounds like you were given a side quest by the goblin guarding the bridge: give me your username and password, use a password manager, solve this CAPTCHA, go there to fetch me a Two Factor Authentication code. Login to a dozen sites every day and your sanity starts fraying fast. Little wonder people will cut corners whenever they can.
In short, WebAuthn is good security because you don't have to think about it. It's secure, it's easy to use, it works the same on every site and it does away with the whole site login circus act. I don't know about you, but I'm looking forward to anything that can make my life a little bit simpler, especially after the crazy year 2020 has been.
Stay safe, online and offline!
Some articles published on the Joomla Community Magazine represent the personal opinion or experience of the Author on the specific topic and might not be aligned to the official position of the Joomla Project
By accepting you will be accessing a service provided by a third-party external to https://magazine.joomla.org/
 Community Magazine
Community Magazine 
Comments 1
Another fantastic contribution, thank you so much for this code and also for the excellent, detailed explanation.